Configuration
Prepare¶
Execute the installation script to download only the environment and save it to dist.
curl -sSL https://gitlab.phaidra.org/fair-data-austria-db-repository/fda-services/-/raw/release-1.11/install.sh | DOWNLOAD_ONLY=1 bash
Static Configuration¶
Call the helper script to regenerate the client secret of the dbrepo-client and set it as value of the
AUTH_SERVICE_CLIENT_SECRET variable in the .env file.
Update the rest of the default secrets in the .env file to secure passwords. You can use openssl for that, e.g.
openssl rand -hex 16. Set auth_ldap.dn_lookup_bind.password in dist/rabbitmq.conf to the value of
SYSTEM_PASSWORD.
Only set the BASE_URL environment variable in .env when your hostname is not localhost.
Runtime Configuration¶
Auth Service¶
The Auth Service can be configured easily when DBRepo is running. Start DBRepo temporarily:
docker compose up -d
Log into the Auth Service with the default credentials admin and the value of AUTH_SERVICE_ADMIN_PASSWORD
(c.f. Figure 1) and select the "dbrepo" realm . In the sidebar, select the
"User federation" and from the provider list, select the "Identity Service" provider
.
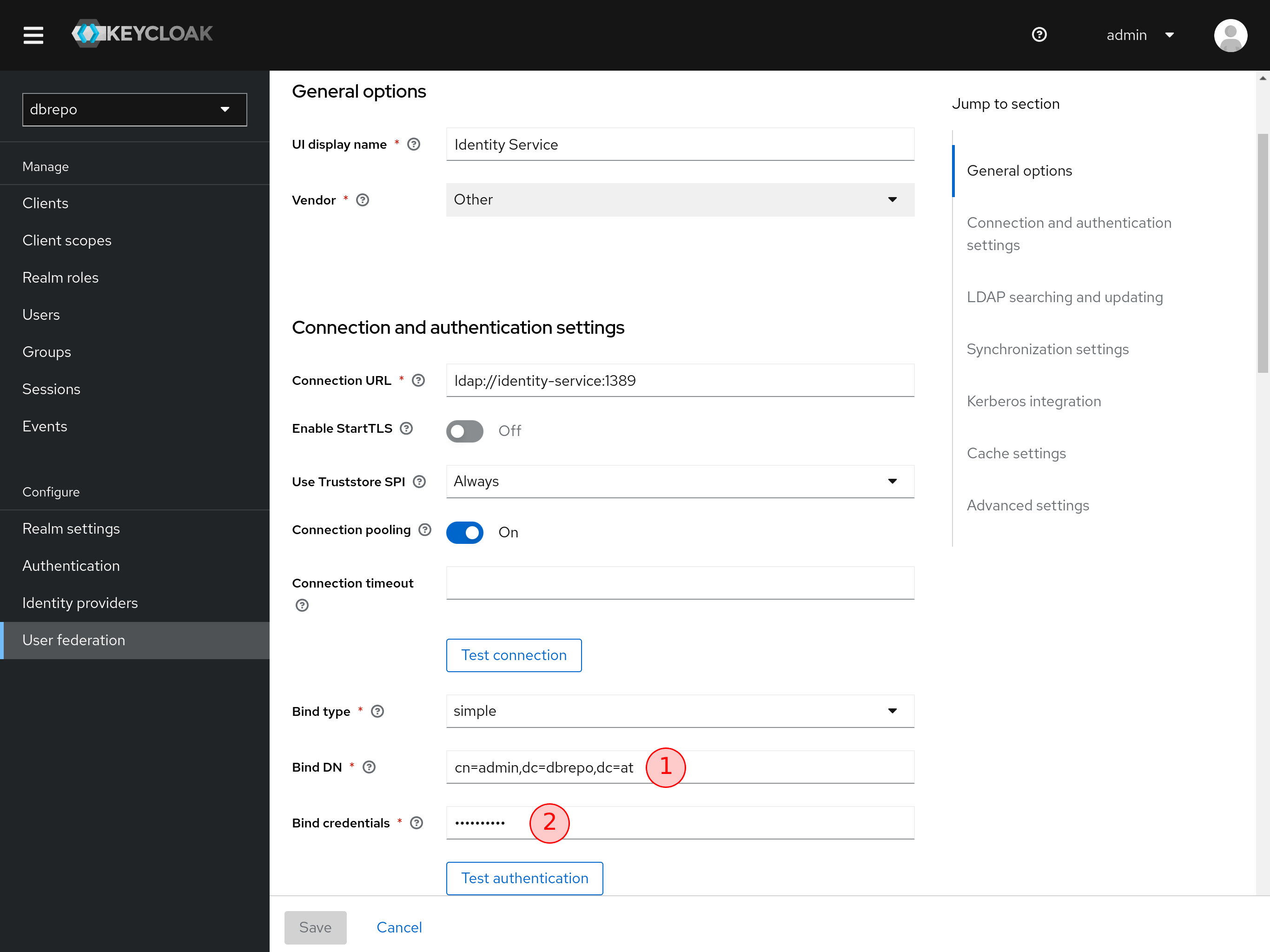
If you plan to change the default admin username (c.f. Figure 2), modify the Bind DN
but this is optional. Change the Bind credentials to the desired password from
the variable IDENTITY_SERVICE_ADMIN_PASSWORD in .env.
Update the client secret of the dbrepo-client:
curl -sSL "https://gitlab.phaidra.org/fair-data-austria-db-repository/fda-services/-/raw/release-1.11/.scripts/reg-client-secret.sh" | bash
Gateway Service¶
Also, update the JWT key according to the Keycloak documentation. To secure your deployment traffic with SSL/TLS, tell the Gateway Service to use your certificate secret (e.g. from Let's Encrypt):
services:
...
dbrepo-gateway-service:
...
volumes:
- /path/to/cert.crt:/app/cert.crt
- /path/to/cert.key:/app/cert.key
...
Now redirect all non-HTTPS routes to HTTPS in the Gateway Service:
server {
listen 80 default_server;
server_name _;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl default_server;
server_name my_hostname;
ssl_certificate /app/cert.crt;
ssl_certificate_key /app/cert.key;
...
}
Apply the Configuration¶
Restart the configured DBRepo system to apply the static and runtime configuration:
docker compose down
docker compose up -d
The secure installation is now finished!
Next Steps¶
You should now be able to view the front end at http://localhost.
Please be warned that the default configuration is not intended for public deployments. It is only intended to have a
running system within minutes to play around within the system and explore features. It is strongly advised to change
the default .env environment variables.
Next, create a user account and then create a database to import a dataset.